VPN obfuscation: Using a virtual private network (VPN) is always a smart option. It conceals your identity, encrypts the data you send and receive online, sidesteps censorship on the internet, and enables you access to stuff that is normally unavailable to you. Unfortunately, governments and online providers have developed the ability to detect and stop VPN traffic.
When website administrators and network administrators began attempting to install new and improved anti-VPN methods, VPN service providers began offering features that may circumvent these bans. Obfuscation of VPN traffic, also known as traffic obfuscation, VPN cloaking, or stealth VPN, is one of these features. But what do all of these words and phrases actually mean?
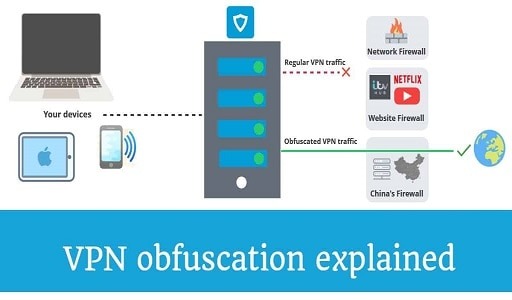
What is VPN Obfuscation?
The term “VPN obfuscation” refers to the collection of elements that masquerade VPN communication as standard internet traffic. This enables customers to get over VPN barriers and utilize a VPN service even when they are in an area with extremely stringent regulations, such as China.
Think about how information moves around on the internet to have a better understanding of how the process works. Along its journey from the origin to the destination, each and every piece of data is divided into a number of discrete units known as packets. These data packets include not only the raw content but also the metadata regarding the type of protocol that was used to deliver the data.
When you use a virtual private network, or VPN, to encrypt your traffic, websites and online services may detect traces of the VPN and refuse to grant you access to their platforms. They are able to accomplish this by inspecting the patterns of encryption and locating distinct VPN signatures.
Through the use of VPN obfuscation, all of the VPN metadata is removed from the data packet. This ensures that VPN blockers and firewalls are unable to determine that you are making use of a VPN and instead allow the packets to be treated as regular internet traffic.
Obfuscation can be achieved by VPN service providers through the utilization of specialized obfuscated servers, proxies, and stealth protocols that hide the use of VPNs. How exactly do they function, and what advantages do they have over standard VPN servers to offer users?
How exactly does obfuscation work?
It is essential to be familiar with the operation of a virtual private network (VPN) in order to comprehend obfuscation. When you connect to a virtual private network (VPN), the data you send through a VPN tunnel is encrypted. During this process, it additionally obtains a one-of-a-kind encryption pattern as well as a distinct VPN signature. The data is safe, but some firewalls and anti-VPN software can detect when a VPN is being used and block access to the websites and services that require it as a result.
Obfuscation of a VPN involves removing any data relevant to the VPN from the data packets, making it impossible for anyone to determine that the data originated from a VPN. It is the goal of an obfuscated server, also known as a stealth VPN, to disguise the true nature of its traffic so that it appears to be identical to that of a typical internet connection.
Obfuscation can be accomplished by VPN service providers in a number of different methods.
-
OpenVPN Scramble
OpenVPN Scramble is a patch that is open-source and disguises the communication that is sent through OpenVPN. It is also known as the XOR obfuscation. It does this by utilizing the XOR additive cipher, which changes the value of each bit in a data packet, rendering the packet worthless for Deep Packet Inspection (DPI).
Obfuscation can be achieved by the use of the OpenVPN Scramble technique, although this method is not a failsafe. The XOR cipher is a fairly straightforward technique that can be easily broken by more sophisticated VPN-blocking algorithms. It may be beneficial for users who reside in nations that do not place limitations on internet access, but it is not particularly effective when used against more advanced firewalls.
-
Obfsproxy
Obfsproxy, also known as an obfuscated proxy, is a subproject of Tor that was developed to circumvent restrictions imposed by the Tor browser. The way it works is by transforming the normal HTTP traffic that you send over the internet into something more secure and putting that in a layer of protection. Although obfsproxy was originally designed for use with the Tor browser, some virtual private networks (VPNs) have adapted it so that it may be used with OpenVPN.
In addition, Obfsproxy uses a peculiar handshake, which is the first data packet sent while establishing a connection, and it does not contain a byte sequence that is easily identifiable. Despite the fact that this safeguards your communications, the artificial randomness can make it easier for ISPs and websites to identify and obfuscate proxy traffic.
-
Shadowsocks
Another open-source obfuscation approach that allows VPN providers to get around VPN bans is called Shadowsocks. A computer programmer from China came up with the idea to get through the Great Firewall of China, which is one of the most extensive forms of online censorship anywhere in the world.
Shadowsocks is an anonymizing proxy that hides VPN traffic by making it look like regular HTTPS communication. In most cases, VPN blockers will not interfere with HTTPS traffic since they do not believe it poses a security risk. Shadowsocks, in contrast to the other approaches, can be utilized not just with OpenVPN but also with the WireGuard protocol, which was developed relatively recently.
-
OpenVPN Over SSL
The OpenVPN over SSL protocol encrypts the OpenVPN traffic and sends it through an additional layer of protection provided by SSL. This means that the VPN encryption process itself is encrypted, making it impossible for even DPI to identify the traffic as coming from a VPN.
This method of obfuscating VPN traffic is not suited for the typical user and is utilized by VPN services only very infrequently. In order to conceal VPN use, both the user and the VPN provider need to install and configure a piece of open-source software known as Stunnel on their respective servers and devices.
Why is Obfuscated Servers necessary?
Users may find that obfuscated servers do not meet their needs. They are more difficult to configure and can be significantly slower than normal servers. Obfuscated servers are sometimes the sole way to access restricted content; however, there are times when this is not the case. Here are some of the possible reasons why you will need them:
- Avoid VPN blocks: The usage of virtual private networks (VPNs) is restricted or outright prohibited in several nations, including China, Iran, and North Korea. If you currently reside in one of these countries or have plans to travel there in the near future, using obfuscated servers may be your only option for getting around VPN restrictions.
- Preserve your privacy: Obfuscation is useful in situations in which you require an increased level of privacy. Your information is given an additional layer of security without the ISP or network administrators being aware that you are using a virtual private network (VPN).
- Avoid censorship: Particular nations place significant barriers in the way of users’ ability to access certain websites and online services. The use of a standard VPN ought to be sufficient to circumvent these limitations; nonetheless, Internet service providers (ISPs) and network administrators frequently go to tremendous pains to prohibit VPN traffic entirely. You can access whatever content you want while hiding the fact that you’re using a virtual private network (VPN) thanks to obfuscated servers.
Gain an Additional Layer of Defense with Obfuscated Servers
You will be able to access content that is restricted by your Internet service provider (ISP), government, workplace, or school if you use a virtual private network (VPN) that has obfuscated servers. Nevertheless, only a few VPN services actually offer this capability. Make sure the VPN service you choose has obfuscation as an added function if you want to reap the benefits of this privacy-enhancing technology (VPN obfuscation).
Would you like to read more about VPN obfuscation-related articles? If so, we invite you to take a look at our other tech topics before you leave!










