The National Security Agency (NSA) isn’t exactly known for sharing information about vulnerabilities they discover. In fact, they kept the Microsoft bug known as Eternal Blue a secret for at least five years to exploit it as part of their digital espionage. (At least, you know, until it was eventually discovered and released by hackers). How To Fix Windows 10 Vulnerability.
But maybe they’ve had a change of heart. (If you truly believe that I have a bridge to sell you.)
In an uncharacteristic show of transparency, the NSA recently announced a major public key infrastructure (PKI) security issue that exists in Microsoft Windows operating systems that’s left more than 900 million PCs and servers worldwide vulnerable to spoofing cyberattacks. This vulnerability is one of many vulnerabilities Microsoft released as part of their January 2020 security updates. Maybe they didn’t want a repeat of the last incident. Whatever the reason, we’re just glad they decided to disclose the potential exploit.
This risk of this vulnerability boils down to a weakness in the application programming interface of Microsoft’s widely used operating systems. But what exactly is this Windows 10 vulnerability? How does it affect your organization? And what can you do to fix it? Let’s hash it out.
What’s the Situation with This Windows 10 Vulnerability?
Windows 10 has been having a rough go of things these past several months in terms of vulnerabilities. In the latest Window 10 vulnerability news, the NSA discovered a vulnerability (CVE-2020-0601) that affects the cryptographic functionality of Microsoft Windows 32- and 64-bit Windows 10 operating systems and specific versions of Windows Server. Basically, the vulnerability exists within the Windows 10 cryptographic application programming interface. What’s also known as CryptoAPI (or what you may know as the good ol’ Crypt32.dll module) affects how it validates elliptic curve cryptography (ECC) certificates. How To Fix Windows 10 Vulnerability
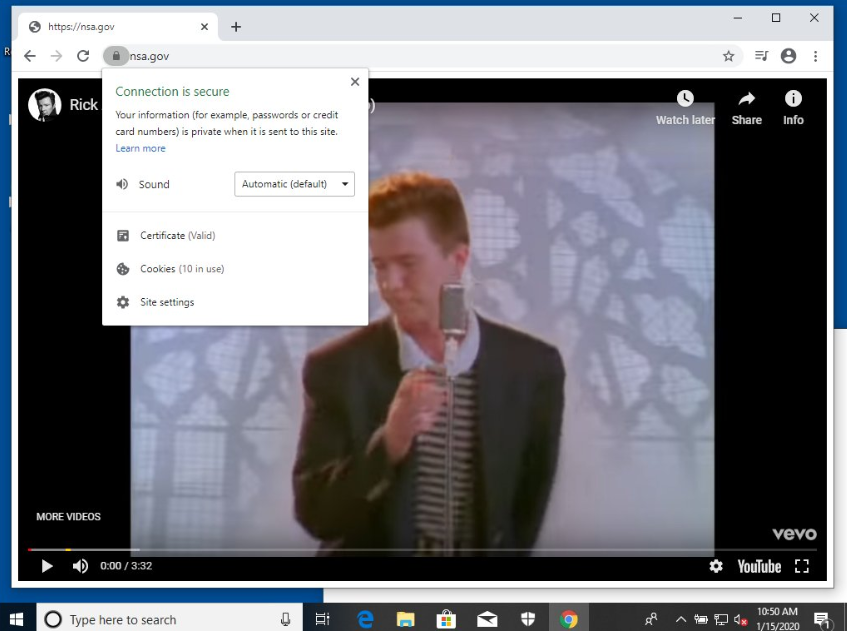
What it does, in a nutshell, is allow users to create websites and software that masquerade as the “real deals” through the use of spoofed digital certificates. A great example of how it works was created by a security researcher, Saleem Rashid, who tweeted images of NSA.com and Github.com getting “Rickrolled.” Essentially, what he did was cause both the Edge and Chrome browsers to spoof the HTTPS verified websites.
Although humorous, Rashid’s simulated attacks are a great demonstration of how serious the security flaw is. Spoofing a digital certificate to exploit the security flaw in CryptoAPI means that anyone can pretend to be anyone — even official authorities.
How To Fix Windows 10 Vulnerability
CryptoAPI is a critical component of Microsoft Windows operating systems. It’s what allows developers to secure their software applications through cryptographic solutions. It’s also what validates the legitimacy of software and secure website connections through the use of X.509 digital certificates (SSL/TLS certificates, code signing certificates, email signing certificates, etc.). So, basically, the vulnerability’s a bug in the OS’s appliance for determining whether software applications and emails are secure and whether secure website connections are legitimate.
So, what the vulnerability does is allow actors to bypass the trust store by using malicious software that is signed by forged/spoofed ECC certificates (doing so makes them look like they’re signed by a trusted organization). This means that users would unknowingly download malicious or compromised software because the digital signature would appear to be from a legitimate source.
This vulnerability can cause other issues as well, according to the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA):
This could deceive users or thwart malware detection methods such as antivirus. Additionally, a maliciously crafted certificate could be issued for a hostname that did not authorize it, and a browser that relies on Windows CryptoAPI would not issue a warning, allowing an attacker to decrypt, modify, or inject data on user connections without detection.”
Does This Mean ECC Is Not Secure?
No. This flaw in no way, shape, or form affects the integrity of ECC certificates. It does, however, cast a negative light on Windows’ cryptographic application programming interface shines a spotlight on the shortcomings of its validation process.
Let me reiterate: This is a flaw concerning Windows CryptoAPI and does not affect the integrity of the ECC certificates themselves. If you’re one of the few using ECC certificates (you know, since RSA is still the more commonly used than ECC), this doesn’t impact the security of your certificates. How To Fix Windows 10 Vulnerability. The patch from Microsoft addresses the vulnerability to ensure that Windows CryptoAPI fully validates ECC certificates.
What This Windows 10 Vulnerability Means for Your Organization
![]()
Basically, this cryptographic validation security flaw impacts both the SSL/TLS communication stream encryption and Windows Authenticode file validation. Malicious actors who decide to exploit the CryptoAPI the vulnerability could use it to:
- defeat trusted network connections to carry out man-in-the-middle (MitM) attacks and compromise confidential information;
- deliver malicious executable code;
- prevent browsers that rely on CryptoAPI from validating malicious certificates that are crafted to appear from an unauthorized hostname; and
- appear legitimate and trusted entities (through spoofing) to get users to engage with and download malicious content via email and phishing websites.
The NSA press release states:
NSA assesses the vulnerability to be severe and that sophisticated cyber actors will understand the underlying flaw very quickly and, if exploited, would render the previously mentioned platforms as fundamentally vulnerable. The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available. Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners.”
Steps to Take to Mitigate This Bug
Wondering what you should do to mitigate the threat on your network and devices? The NSA has a few recommendations:
Get to Patchin’ ASAP
The NSA recommends installing a newly-released patch from Microsoft for Windows 10 operating systems and Windows Server (versions 2016 and 2019) as soon as possible on all endpoints and systems. Like, right now. Get to it! As a best practice, you also can turn on automatic updates to ensure that you don’t miss key updates in the future.
According to Microsoft’s Security Update Guide:
After the applicable Windows update is applied, the system will generate Event ID 1 in the Event Viewer after each reboot under Windows Logs/Application when an attempt to exploit a known vulnerability ([CVE-2020-0601] cert validation) is detected.”
Here at The SSL Store, we’ve already rolled out the patch to ensure that all of our servers and endpoint devices are protected. (Thanks, Ross!) However, rolling out these kinds of updates is something you don’t want to wait around to do because it leaves your operating systems — and everything else as a result — vulnerable to spoofing and phishing attacks using spoofed digital certificates.
Prioritize Your Patching Initiatives
But what if you’re a major enterprise that can’t just get it done with a snap of the fingers? (Yeah, we know how you big businesses sometimes like to do things.) In that case, they recommend prioritizing patching your most critical endpoints and those that are most exposed to the internet. Basically, patch your mission-critical systems and infrastructure, internet-facing systems, and networked servers first.
Implement Network Prevention and Detection Measures
For those of you who route your traffic through proxy devices, we have some good news. While your endpoints are getting patched, your proxy devices can help you detect and isolate vulnerable endpoints. That’s because you can use TLS inspection proxies to validate SSL/TLS certificates from third parties and determine whether to trust or reject them.
You also can review logs and packet analysis to extract additional data for analysis and check for malicious or suspicious properties.
Would you like to read more Windows Operating System-related articles? If so, we invite you to take a look at our other tech topics before you leave!
![]()