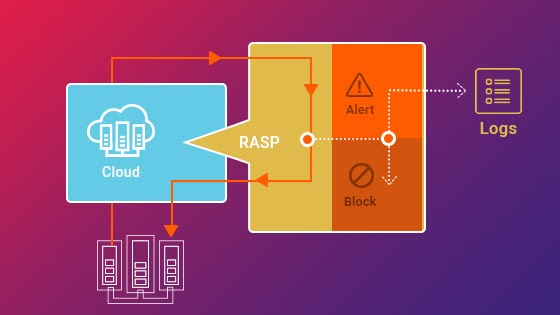
Runtime Application Self-protection Strategy: The runtime application self-protection strategy is a new security approach that will assist organizations in dealing with complex hacking threats and ensuring that their data and apps are not hacked. This is believed to be the best way for building a high-quality runtime environment in which anything is capable of adjusting a higher amount of functionality without causing any problems.
However, this is widely regarded as the most effective approach for incorporating protection into a working program, irrespective of where it exists on the server, guaranteeing that there are no issues at any time and that the desired consequences are easily achieved. This is viewed as the best way to detect, block, and gather hazards as rapidly as possible, assuring that there should be no issues in a timely manner and that intended objectives may be achieved without the trouble.
The use of the program in a consistent environment is viewed as the most effective means of monitoring its activity, allowing businesses to protect the program from cybersecurity incidents and a range of other dangerous impulses throughout the process without the requirement for human intervention.
RASP security also referred to as runtime application protection, is an excellent way for organizations to manage difficulties quickly and without creating network slowness or content difficulties. With the help of this technology, traffic inspection will be incredibly uncomplicated, and we will possess a comprehensive grasp of how traffic and details are incorporated into the numerous applications in the sphere of dealing with such problems.
This is thought to be one of the best possible security processes that businesses can use to improve the durability of their connections and ensure that they will not be canceled at any point.
You may also like 8 Best Things to Develop ShopWare for your eCommerce Store
The following are the features and procedures associated with the implementation of runtime application self-protection technologies.
Runtime Application Self-protection Strategy
The runtime application self-protection architecture is the greatest effective mobile app security, as it will be capable of analyzing calls from the program to the gadget while also taking fantastic care of the aspects that will be very secure and safeguarded. It will additionally aid in the straight processing of data queries within the application, as well as delivering a considerable improvement in overall application security by constantly assessing inputs and easily preventing hazardous inputs.
This is believed to be the best way for preventing unwanted alterations and adjustments to the runtime environment, guaranteeing that the whole process works properly and that the intended security and accessibility consequences are reached. The following are the primary characteristics of this concept:
- It will be based on the highest possible application protection, which will help to minimize application flaws from being attacked while retaining the application’s licensed functionality.
- It will be based on the right kind of application threat data, providing security experts with the knowledge they need to know about who is attacking and what techniques they’re using, and enabling applications to be specifically targeted at the programming levels without trouble.
The following are the most significant rewards of depending on this strategy’s implementation in favor of companies:
- The self-protection mechanism for runtime programs will always support in offering a much bigger perspective of the circumstance, ensuring that consistency is maintained and that no concerns arise at any period. This functionality has the capability to provide alternatives a considerable boost by enabling intrusions to be handled with rapid and effective vulnerability fixing.
- This is believed to be the best possible means of guaranteeing that everything remains substantially less expensive in terms of installation when contrasted to other available techniques such as WAF.
- This system’s implementation will therefore guarantee that implementation can be performed swiftly and efficiently on existing servers, with no financial expenditure required on the part of organizations.
- Runtime application self-protection techniques will potentially give technologically advanced platforms a boost, enabling the model building, verification, and human resource deployment all at the same time.
- This section will have a high level of accuracy, so there would be no issues at any point in time, and legacy techniques will be processed fast and without difficulties. It’s crucial to have a clear understanding of the application’s functionality so that network protection can be addressed swiftly and tracking can be conducted without creating any issues.
- It will help businesses improve their performance in the domain of changing the adoption equation so that they can reliably secure more details and a wider range of applications without spending a lot of resources.
- This concept may easily manage rapid development, web applications, and cloud-based technology. It will also be effective in accelerating the production procedure within the organization, removing the need for continuous statistical platform recapitalization and enabling other platforms to run simultaneously without trouble. As a consequence, the accuracy component will significantly improve.
- This strategy will also aid businesses in adhering to the company’s top priority-based processes and establishing the right amount of coding protections. This is believed to be the most practical method as an enterprise app security for swiftly acquiring actionable security information, guaranteeing that basic objectives are satisfied and that prospective people are not distracted at any time.
You may also like Javascript Security: What Should You Know?
As a consequence, developing a greater level of accuracy in the architectural structure is intimately linked with the implementation of runtime application self-protection, ensuring that the targeted objectives are completely fulfilled and that no concerns arise for the parties concerned at any point. Companies would be wise to depend on the implementation of runtime application self-protection because it will aid them in getting useful recommendations throughout the process.
This is regarded to be the best way for highlighting upgrades and ensuring that security is made uncomplicated in terms of controlling functionality without problems. As an outcome, depending on the appealing company’s appropriate version of the implementation of runtime application self-protection is the best possible assessment that organizations can make such that real-time inspection can be accomplished with ease and constant functionality can be achieved without raising any concerns in the minds of responsible customers. Mobile application security is very much needed in our society. So every organization should implement this innovation in their business.
Would you like to read more about Runtime Application Self-protection Strategy-related articles? If so, we invite you to take a look at our other tech topics before you leave!