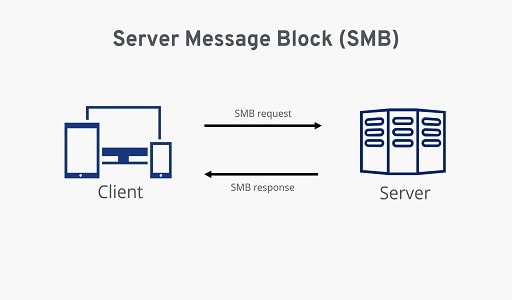
When many computers are linked to the same network, a protocol known as SMB (Server Message Block) enables them to share their files and hardware (such as printers and external hard drives).
Since more and more people use the SMB protocol, the number of malicious attacks that target it has also increased. Because its older versions do not use encryption, the SMB protocol is susceptible to cyberattacks. This means that any hacker who understands how to exploit it can gain access to your files and data.
In addition, there are additional dangers connected with using SMB, which is why it is vital to have an understanding of how the protocol operates, the various varieties it comes in, and how to protect yourself.
What is SMB (Server Message Block)?
Server Message Block is what “SMB” stands for. It is a network protocol that allows computers and other devices connected to a local or wide area network to communicate data with one another. The protocol makes it possible for computers on a local network to exchange resources including files, printers, and other devices with one another.
IBM initially developed SMB in the middle of the 1980s in order to facilitate file sharing in DOS. Since then, however, it has been adopted by a wide variety of other operating systems, including macOS, Linux, and Microsoft’s Windows.
Because it streamlines the process of accessing information and resources stored on other computers on a network, the Server Message Block (SMB) protocol is an essential component of many day-to-day operations carried out by companies and other organizations.
How to send big files securely with top-of-the-line security measures.
Suppose that you are part of a team that operates virtually, with members working from their homes or other remote locations. In situations like this, the SMB protocol is an excellent approach to rapidly and easily share data with others. It will make it possible for all members of the team to access the same data and work cooperatively on projects. It is possible for many users to remotely see and modify the same file as if it were locally stored on their own computers.
How does the Server Message Block Protocol work?
In order to establish a connection between the client and the server, the SMB protocol uses a mechanism that is based on a request and a response. The following are the stages involved in its operation:
1. Client request: The client (the device making the request) sends a request to the server using SMB packets. The packet contains the full path of the requested file or resource.
2. Response from server: The server (the device with access to the requested file or resource) evaluates the request and, if successful, responds back with an SMB packet containing more information on how to access the data.
3. Process by Client: The client receives the response and then processes the data or resource accordingly.
Let’s look at an example of this to better comprehend it. Imagine that you need to print a paper from your cabin, but the printer is located in another part of the office. As soon as you give the command to print the document, your computer, which acts as the client, will send the request to print it using SMB packets to the printer, which acts as the server. The printer will assess the request and then report back using the SMB packets about the status. For example, it will indicate if the document is printing, whether it is in a queue for printing, or whether it cannot be printed because of a printer error.
Types of SMB Protocol
As a result of developments in technology, the SMB protocol has also undergone a few iterations of improvement. The following is a list of the numerous kinds of SMB protocols that are available today:
SMB Version 1:
This is the first version of the SMB protocol, which was released by IBM in 1984 so that DOS users could share files with one another. After some time, Microsoft changed it so that it could be used on Windows.
CIFS:
Common Internet File System (CIFS) is a modified version of SMBv1, which was primarily developed to facilitate the sharing of larger files. This was the primary motivation behind the development of CIFS. It was initially made available with Windows 95.
SMB Version 2:
SMB version 2, which was published by Microsoft in conjunction with Windows Vista in 2006, is a successor to the earlier versions that is both more secure and more effective. This protocol offered features such as improved authentication, larger packet size, fewer commands, and higher efficiency. These characteristics were all introduced in addition to the fact that the packet size was increased.
SMB Version 3:
With the release of Windows 8, Microsoft made SMB version 3 available. It was conceived with the intention of enhancing performance while also incorporating support for end-to-end encryption and enhanced authentication procedures.
SMB Version 3.1.1:
The most recent version of the SMB protocol was made available in conjunction with the release of Windows 10 in 2015, and it is backward-compatible with all earlier versions. It provides additional security measures, such as AES-128 encryption and enhanced security features for warding off hostile assaults, and it also improves the performance of existing security features.
What are the risks associated with using the SMB Protocol?
There are significant security issues linked with the SMB protocol, despite the fact that it has proven to be a very beneficial asset for a great number of companies. In order to break into business systems and networks, hackers have focused their attention on this protocol. Cybercriminals have made it one of the most prevalent attack vectors they utilize to break into company networks and systems.
The situation is made worse by the fact that, despite the availability of improved versions of SMB, a significant number of Windows machines are still operating on the more insecure versions 1 or 2. Because of this, the likelihood of hostile actors acquiring access to sensitive data through the exploitation of these devices has increased.
The following is a list of the most popular SMB exploits:
Brute Force Attacks
Brute force assaults are one of the most popular types of attack vectors that hackers employ against the SMB protocol. Hackers will use automated tools in these types of attacks to try to guess the correct combinations of usernames and passwords. After they have gained access to the network, they have the ability to steal sensitive data or install dangerous malware on the system.
Ransomware Attacks
Attacks using ransomware are another significant danger to the SMB protocol. Hackers use this tactic to steal money by encrypting the information that is held on a system and then holding it hostage until they get paid in exchange for the encryption keys. If the ransom is not paid, they have the option of permanently deleting all of the encrypted material.
Buffer Overflow Attacks
Attacks against the SMB protocol that involve buffer overflow are another type used by hackers. Hackers will send a tremendous volume of data to a system in order to flood its memory with useless information and bring it to a crashing halt during one of these attacks. This method is frequently used to install malicious software within the system, which can then be utilized to obtain access to confidential data or to conduct a denial-of-service attack.
Man-in-the-Middle Attacks
Man-in-the-middle assaults are another vector of attack that can be employed against the SMB protocol. In this scenario, a hacker inserts malicious code into the network, which gives them the ability to eavesdrop on the conversation that is taking place between two different computers. Users are then able to view and make changes to the data that is being transferred.
Remote Code Execution
Another type of attack vector that can be used against the SMB protocol is remote code execution. When an attack of this type occurs, hackers insert malicious code into the system, which gives them the ability to take remote control of the machine. After they have gained access to the system, they are in a position to steal confidential data or exploit other weaknesses in the network.
It is important to maintain safety online while using the SMB Protocol
Even though there are a number of dangers connected with using the SMB protocol, Windows relies heavily on it nonetheless. As a result, it is absolutely necessary to make certain that all corporate systems and networks are protected against intrusion by malicious actors.
You should only utilize the most recent version of the SMB protocol, periodically update your security software, and monitor your network for behaviors that appear to be suspicious in order to maintain your level of protection. In addition, it is essential to educate your employees on the most effective methods for data protection and ensure that all users employ robust passwords. You may assure the continued safety of your company from intrusions by criminal actors by adhering to these precautionary steps.
Would you like to read more about SMB Protocol-related articles? If so, we invite you to take a look at our other tech topics before you leave!