Ransomware attacks pose a significant threat to all of us and have resulted in billions of dollars in damages. The increasing use of ransomware has led to the emergence of various strains of this dangerous malware, including Jigsaw. So, where did Jigsaw ransomware originate from, how does it function, and what measures can you take to avoid it?
How does the Jigsaw Ransomware originate
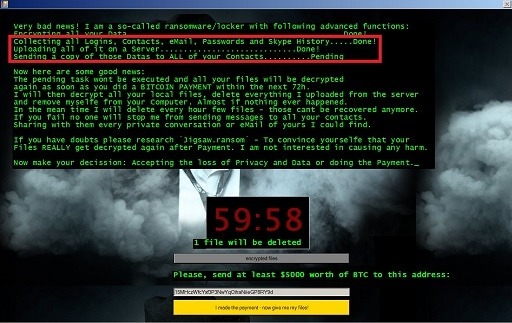
Jigsaw ransomware was first discovered in April 2016. It is named after the fictional character from the horror movie franchise “Saw,” as the malware’s creators used the movie’s imagery in their ransom notes. Jigsaw ransomware is a type of malware that encrypts a victim’s files and demands payment in exchange for the decryption key. It typically demands payment in Bitcoin, which is difficult to trace.
Jigsaw ransomware is a variant of the popular “CryptoLocker” ransomware family. It spreads through malicious email attachments, infected software downloads, or by exploiting vulnerabilities in computer networks. Once it infects a system, Jigsaw starts encrypting files, and displays a ransom note on the victim’s screen, threatening to delete one or more files every hour until the ransom is paid.
One unique aspect of Jigsaw ransomware is that it includes a countdown timer that threatens to permanently delete the victim’s files if the ransom is not paid within the given time limit. The malware also displays a message that taunts the victim and tries to scare them into paying the ransom. Jigsaw ransomware has evolved over the years and has become increasingly sophisticated, making it even more challenging to detect and remove.
New Ransomware Targeting Unpatched Microsoft Exchange Servers
It’s essential to take proactive measures to prevent Jigsaw ransomware from infecting your system. This includes regularly backing up important files, using reputable antivirus software, and being cautious when opening email attachments or downloading software from the internet.
How Does Jigsaw Ransomware Work?
Jigsaw ransomware works by encrypting a victim’s files and then demanding payment in exchange for the decryption key. Here’s a step-by-step breakdown of how Jigsaw ransomware typically operates:
- Infection: Jigsaw ransomware can infect a computer in various ways, including email attachments, infected software downloads, or by exploiting vulnerabilities in computer networks. Once it infects a system, Jigsaw starts to encrypt the victim’s files.
- Encryption: Jigsaw ransomware uses a combination of symmetric and asymmetric encryption algorithms to encrypt the victim’s files. It encrypts files with specific extensions, including documents, photos, videos, and music.
- Ransom Note: Once the encryption process is complete, Jigsaw displays a ransom note on the victim’s screen, demanding payment in exchange for the decryption key. The ransom note typically includes instructions on how to pay the ransom, often in the form of Bitcoin.
- Countdown Timer: One unique feature of Jigsaw ransomware is that it includes a countdown timer that threatens to permanently delete the victim’s files if the ransom is not paid within the given time limit. The timer usually starts at one hour and decreases by one file for every hour that passes.
- Deletion: If the victim fails to pay the ransom within the given time limit, Jigsaw ransomware will start to delete the victim’s files systematically. The malware will delete one or more files every hour until the ransom is paid or all the victim’s files are deleted.
Jigsaw ransomware is a particularly nasty form of malware that can cause significant damage to individuals and organizations. Therefore, it’s crucial to take proactive measures to protect your computer system from this threat, such as using reputable antivirus software, keeping your software updated, and regularly backing up your important files.
What Are Jigsaw’s Weaknesses?
Jigsaw ransomware has evolved over the years and has become more sophisticated, making it difficult to detect and remove. However, there are some weaknesses that may be exploited to help protect against it. Here are some of the known weaknesses of Jigsaw ransomware:
- No Encryption Key Exchange: Jigsaw ransomware does not exchange encryption keys with a remote server, meaning the key is stored locally on the infected system. This creates an opportunity for victims to recover their files without paying the ransom by attempting to locate the key.
- Time-Based Deletion: Jigsaw ransomware uses a countdown timer that deletes files at set intervals if the ransom is not paid. However, this feature can be disabled by setting the system clock back to a time before the malware infected the computer.
- Outdated Code: Jigsaw ransomware has been around for a while, and its code has not been updated significantly in recent years. This means that some antivirus software can detect and remove it effectively.
- Vulnerability Exploits: Like most malware, Jigsaw ransomware may exploit vulnerabilities in software or operating systems to gain access to a computer system. Keeping software updated with the latest patches and security fixes can help reduce the risk of infection.
- Decryption Tools: Over the years, security researchers have developed several decryption tools that can recover files encrypted by Jigsaw ransomware. While not foolproof, these tools may help some victims recover their files without paying a ransom.
While it’s crucial to take proactive measures to protect against Jigsaw ransomware, such as regularly backing up files and using reputable antivirus software, it’s also essential to understand the weaknesses of the malware. Doing so can help you take steps to reduce the risk of infection or mitigate damage in the event of an attack.
How to Avoid Jigsaw Ransomware
Jigsaw ransomware can cause significant damage to individuals and organizations. Therefore, it’s essential to take proactive measures to avoid becoming a victim of this malware. Here are some steps you can take to avoid Jigsaw ransomware:
- Be cautious when opening email attachments: Jigsaw ransomware often spreads through malicious email attachments. Therefore, it’s crucial to be cautious when opening attachments, particularly those from unknown senders or those that seem suspicious.
- Use reputable antivirus software: A good antivirus software can detect and remove Jigsaw ransomware, as well as other forms of malware. Therefore, it’s essential to use reputable antivirus software and keep it up-to-date.
- Keep software up-to-date: Outdated software can have vulnerabilities that may be exploited by Jigsaw ransomware. Therefore, it’s important to keep the software, particularly operating systems and web browsers, up-to-date with the latest security patches and updates.
- Back up important files regularly: Regularly backing up your important files can help protect them from Jigsaw ransomware. If your files are encrypted by malware, you can restore them from a backup, rather than paying the ransom.
- Avoid downloading software from untrusted sources: Jigsaw ransomware often spreads through infected software downloads. Therefore, it’s essential to avoid downloading software from untrusted sources and only download software from reputable websites.
- Be cautious when clicking on links: Jigsaw ransomware may also spread through links on websites or in emails. Therefore, it’s important to be cautious when clicking on links, particularly those from unknown senders or those that seem suspicious.
By taking these steps, you can significantly reduce the risk of becoming a victim of Jigsaw ransomware. However, it’s important to remain vigilant and stay up-to-date on the latest security threats and best practices for protecting your computer system.
Jigsaw Malware has weaknesses but it can still attack you
Jigsaw ransomware can still be a threat to individuals who are not tech-savvy, even though it can be decrypted. If someone is unaware of the Jigsaw decryptor, this malware could potentially result in the loss of their data and finances. Therefore, it’s advisable to take preventive measures to avoid ransomware infection from the beginning, rather than dealing with the consequences after it has already damaged your computer.
Would you like to read more about Jigsaw Ransomware-related articles? If so, we invite you to take a look at our other tech topics before you leave!
![]()













