DLL hooking is a technique used by developers to add functionality to a program when they don’t have access to its source code. However, it can also be used maliciously by hackers to modify or exploit a program’s behavior. DLL hooking essentially involves intercepting calls to DLL functions and redirecting them to custom functions that can perform additional operations before or after calling the original function. While it can be a powerful tool, it should only be used judiciously and with appropriate caution.
What Is a DLL?
A DLL, or Dynamic Link Library, is a type of file that contains code, data, and resources that can be used by multiple programs simultaneously. DLLs are essentially shared libraries of code that can be called by multiple programs at once, rather than having each program include its own copy of the code. This can help to reduce the overall size of programs, improve performance, and make it easier to maintain and update shared functionality.
DLLs can contain a wide range of functionality, including utility functions, database drivers, graphical user interface elements, and more. They are typically created using a programming language such as C or C++ and are designed to be linked dynamically at runtime rather than statically at compile time.
In Windows operating systems, DLLs are a common component of the operating system architecture and are used extensively by both system and application software. However, they are also a common target for malware attacks, as they can be modified to execute malicious code or to intercept system calls and monitor system activity.
What Is DLL Hooking
DLL hooking is a technique used to intercept calls to functions or procedures (collectively known as “APIs”) within dynamic link libraries (DLLs) that are used by other programs. This can be used for various purposes, including modifying the behavior of programs, monitoring and logging system activity, and injecting code into other processes.
The basic idea behind DLL hooking is to replace the original function or procedure with a custom function that performs additional operations before or after calling the original function. This can be done by intercepting the call to the original function and redirecting it to the custom function, which can then perform any necessary operations before or after calling the original function.
There are several methods for implementing DLL hooking, including modifying the import table of a program to redirect calls to a different DLL or function, using Microsoft Detours to intercept function calls, or using inline hooking to redirect the flow of control within a program.
However, DLL hooking can be a powerful tool that can be used for both legitimate and malicious purposes. It can be used to enhance the functionality of existing programs or to monitor and control system activity. On the other hand, malware authors can also use it to gain control over other processes and steal sensitive data. Therefore, it should only be used with caution and only in situations where it is necessary and appropriate.
How Does DLL Hooking Work?
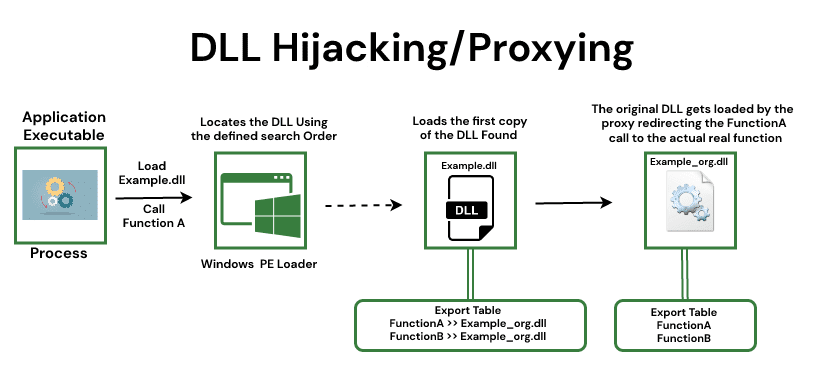
To fully understand how to implement DLL hooking, it’s crucial to grasp the fundamentals. When a program requests a function from a DLL, the operating system searches for the function’s name in the program’s Import Address Table and retrieves the function’s address from the DLL’s Export Address Table. After resolving the address, the program can then execute the function. DLL hooking involves intercepting this process and redirecting the function call to a different function. Although this can be a complex process, there are various commonly used techniques to achieve this. However, it’s worth noting that implementing DLL hooking requires a strong understanding of Windows internals, and may be more suitable for advanced users or Windows power users.
There exist various methods to execute DLL hooking. In the following section, we’ll explore some of the most commonly utilized techniques for its implementation.
IAT Hooking
IAT hooking or Import Address Table hooking is a method of DLL hooking that involves modifying the Import Address Table (IAT) of a program to redirect function calls to a custom function instead of the original function in the targeted DLL.
When a program requests a function from a DLL, the address of the function is stored in the IAT of the program. By modifying the IAT, an attacker can redirect the program to call a custom function instead of the original function. This allows the attacker to intercept the call and perform additional operations, such as logging or modifying the data being passed to or from the function, before or after the original function is called.
IAT hooking can be implemented using a variety of techniques, such as direct modification of the IAT or use of the Microsoft Detours library. However, it can also be used by malware authors to gain control over other processes and steal sensitive data. Therefore, it should be used with caution and only in situations where it is necessary and appropriate.
The following is a typical sequence of events in an IAT hooking attack:
- A program initiates a function call.
- The address of the function is retrieved from the Import Address Table (IAT).
- As the IAT has been hooked, the original function address is modified and points to a malicious function’s memory location.
- The program is redirected to execute the malicious function, which may execute arbitrary code.
- After the malicious function has been executed, the program may then proceed to execute the original function call as intended.
This flow illustrates how an attacker can use IAT hooking to intercept function calls and execute malicious code, potentially leading to unauthorized access, data theft, or other harmful consequences. It is important to note that IAT hooking can be used for legitimate purposes, such as debugging and monitoring applications, but it can also be used maliciously and should be used with caution.
Inline Hooking
Inline hooking is a technique used in software security and system programming that allows modification of the behavior of an application or operating system function by intercepting its execution at runtime.
Unlike other hooking techniques, inline hooking involves replacing the first few bytes of the original function with a jump instruction that redirects the program flow to a custom function, also known as a hook function. The hook function then executes the code it was designed for and returns control to the original function to complete its execution.
Inline hooking can be used to monitor system activity, log information, or modify the behavior of an application or operating system function. For example, it can be used to intercept a function call that opens a file and modify the path of the file before it is opened. However, it can also be used for malicious purposes, such as stealing sensitive data or injecting malware into a system.
Inline hooking requires knowledge of assembly language and low-level system programming, and should only be used by experienced developers or security professionals with a strong understanding of system internals.
Microsoft Detours
Microsoft Detours is a software library that provides a set of APIs for intercepting and instrumenting Win32 functions on Windows operating systems. Detours allow developers to redirect function calls to custom functions, enabling a wide range of functionality such as debugging, tracing, and performance monitoring.
Detours use IAT hooking and inline hooking techniques to achieve their function redirection capabilities. The library works by intercepting function calls at runtime and redirecting them to a detour function, which can then modify the input parameters or return values of the original function, log information, or perform additional operations before or after the original function call.
Detours are widely used in the software industry for a variety of purposes, including debugging and testing, performance profiling, and reverse engineering. However, it can also be used for malicious purposes, such as injecting malware into a system or stealing sensitive data. As with other hooking techniques, Detours should only be used by experienced developers or security professionals with a strong understanding of system internals and programming.
Protect yourself against DLL Hooking
When used properly, DLL hooking can be a valuable technique to enhance the functionality of your software or aid in debugging and optimization. However, it is frequently used for malicious purposes, making it critical to adopt and adhere to best security practices to protect your applications from attacks such as hooking and injection. By implementing robust security measures, you can help ensure that your software remains secure and protected from potential threats.
Would you like to read more about DLL Hooking-related articles? If so, we invite you to take a look at our other tech topics before you leave!