Watering Hole Attack: The activity of hunting is where the term “watering hole attack” originated. It is possible for a hunter to determine the most likely destination of the prey, which is typically a body of water, and then set a trap in that location in order to bring down the prey. If everything goes according to the hunter’s plan, the target will eventually give in to the trap of their own free will and fall victim to the hunt.
In the same vein, cybercriminals will use watering hole attacks to set up traps and wait for unsuspecting victims to walk into them. Then, what exactly are these assaults? And what measures can you take to defend yourself against assaults at watering holes?
What is a Watering Hole Attack?
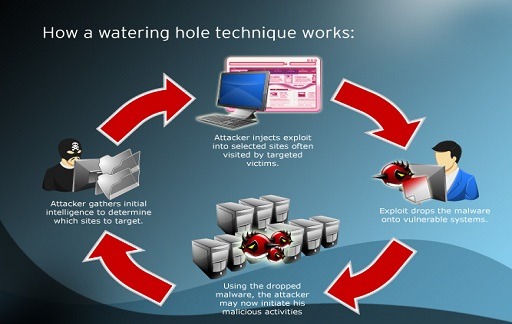
When an adversary conducts a watering hole attack, they aim their attention at a particular website or group of websites that are known to be frequently visited by the individuals whose security they are attempting to compromise. The goal of this cyberattack is to “poison the watering hole” by first compromising the website(s) that are being targeted, and then waiting for victims to visit the compromised website(s) so that malware can be installed on their computers when they do so.
When a watering hole attack is successful, the attacker is able to take control of the systems of the victim, which gives them the ability to steal data or install malicious programs like ransomware or keyloggers. The compromised systems could be used by the attackers to launch additional attacks, such as Distributed Denial of Service (DDoS) or phishing campaigns.
How do attackers typically carry out attacks at watering holes?
Someone Wearing a Mask Observed While Seated in a Chair in Front of a Computer Display
Watering hole attacks are a form of Advanced Persistent Threat (APT) that are utilized by cybercriminals in order to gain access to the network of a particular organization. These attacks get their name from the watering hole concept, suggesting that attackers target a site frequented by a particular group of people to gain access to them.
The most common type of watering hole attack is one where cybercriminals target a website known to be popular among members of a particular organization or demographic. For example, they might focus on an alum website, a site related to a specific industry, or even a social media platform.
Once the attacker has identified the website, they will then inject malicious code into the website. This code may be designed to redirect visitors to a malicious site, deliver malware, steal personal information, or launch further attacks against visitors. In some cases, the malicious code may take advantage of flaws in the website’s security system and exploit it for access to the visitor’s computer.
Note that hackers can also use watering hole attacks against organizations’ websites. In this case, the attacker may place malicious code on the website and use it to gain access to the organization’s networks.
Notable Examples of Watering Hole Attacks
There have been several notable watering hole attacks over the past few years.
-
Chinese Military Attack
In 2013, the Chinese military was the target of a similar attack. The hackers infiltrated their networks by exploiting a vulnerability in a popular social media site used by members of the military. The attack resulted in the theft of sensitive documents related to the Chinese military’s strategy and operations.
-
TV5Monde Attack
In 2015, the French television network TV5Monde was the target of a watering hole attack. Hackers could gain access to the station’s systems by exploiting a vulnerability in a third-party web application. The hackers then proceeded to delete data, hijack accounts, and disrupt TV5Monde’s programming for more than 17 hours.
-
The U.S. Chamber of Commerce Attack
In 2011, the U.S. Chamber of Commerce was the target of a watering hole attack. The hackers could gain access to the organization’s internal networks by exploiting a vulnerability in their website. They were then able to steal large amounts of confidential information.
-
Reveton Attack
The Reveton attack occurred in 2014. Hackers exploited a Windows vulnerability to install Reveton ransomware on thousands of computers worldwide. The malware would lock users out of their systems until a ransom was paid.
-
Red October Attack
There was also the Red October attack. In 2012, the Russian government launched a massive cyberattack targeting diplomatic, governmental, and scientific research institutions in over 30 countries. The attack was carried out by a group of hackers known as the Red October gang.
-
Pony Botnet Attack
The Pony Botnet attack took place in 2013 and targeted 1.58 million user accounts across various sites, including Facebook, Twitter, and Yahoo. The malicious software was designed to steal information from user accounts and send it to remote servers.
-
VPNFilter Attack
In the VPNFilter attack of 2018, the FBI warned that a strain of malware called VPNFilter had infected over 500,000 home and small office routers around the world. The malware collected personal information, launched DDoS attacks, and even manipulated data on infected devices.
How to protect yourself from Watering Hole attacks?
It’s easy to understand why watering hole attacks are so dangerous and why you should be worried about them. They can cause significant damage to your systems and networks and also steal confidential data such as credit card numbers, passwords, and other personal information.
You are fortunate in that you have the ability to defend yourself against attacks of this nature. Here are some pointers to consider:
- Keep an eye out for any strange activity on your network as well as any changes in its performance.
- Maintaining an up-to-date system can be as simple as applying security patches on a regular basis.
- Utilize a Web Application Firewall, also known as a WAF, to protect yourself from known dangers.
- Acquaint yourself and your employees with the most up-to-date safety precautions.
- Examine the regulations governing access control on a regular basis and check to see that they are being followed.
- Always make use of some form of encryption.
- Install software that protects against malware and viruses.
- Utilize an approach to security that is composed of multiple layers.
Implementing these precautions will help you stay safe and reduce the likelihood that you will be the target of an attack, despite the fact that no system can ever be completely secure.
Attacks aimed at drying up the Watering Hole
Because watering hole attacks offer such a significant risk to companies, organizations, and individual users alike, it is absolutely necessary to take precautions to ward off these kinds of cyberattacks.
Make sure that all of the systems are patched and updated with the most recent security updates on a regular basis. Stay away from sketchy websites and never click on unknown links or attachments. Use secure passwords at all times, and if possible, implement two-factor authentication. Also, give some thought to protecting your network from malicious code and unauthorized access by implementing web application firewalls or some other type of security solution.
Would you like to read more about Watering Hole Attack-related articles? If so, we invite you to take a look at our other tech topics before you leave!
![]()