Leaving your house door open is not a security problem until somebody enters through it. Until the existing vulnerabilities in systems are exploited, especially by cybercriminals, they are not an issue.
Intrusion can be avoided by detecting and patching loopholes within your system, and that’s where vulnerability remediation can help. How does it work, precisely?
What is vulnerability remediation?
Remediation of vulnerabilities involves the different ways and means by which such potential loopholes in a system, application, or even a network are located to come up with proper ways in which they may be resolved to avoid any attacks on information integrity.
It typically involves scanning, assessing the risk, prioritizing, and planning for remediation in several steps of vulnerability remediation. In other words, it finds those vulnerabilities that have the biggest impact on the risk and fixes them effectively and efficiently.
The remediation may involve software patches or updates, configuration of security settings, or reconfiguration of the system or network to eliminate vulnerabilities. Sometimes, extended changes are required, such as hardware or software component replacement or the inclusion of additional controls.
The vulnerability remediation could be achieved through continuous monitoring and testing processes, which allow one to identify newly popped-up vulnerabilities while ensuring the effectiveness of their remediation.
It is a critical aspect of a comprehensive cybersecurity strategy that helps protect sensitive data and systems against cyber threats.
How does vulnerability remediation work?
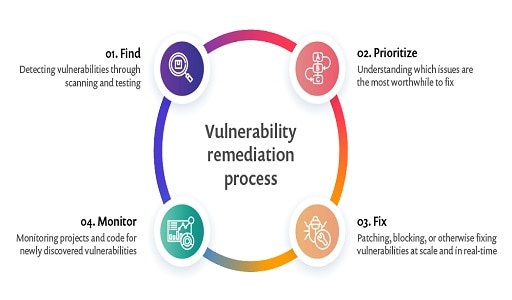
Vulnerability remediation typically follows a structured process that involves the following steps:
Vulnerability Scanning: The first step in vulnerability remediation is to identify vulnerabilities in the system, application, or network. This is typically done using vulnerability scanning tools, which scan the system for known vulnerabilities and report them to the security team.
You can also read: How to Fix Windows 10 Vulnerabilities
Risk Assessment: Once vulnerabilities have been identified, the next step is to assess their potential impact on the organization. This involves analyzing the severity of the vulnerability, the likelihood of it being exploited, and the potential consequences of a successful attack.
Prioritization: Based on the results of the risk assessment, vulnerabilities are prioritized based on their severity and the potential impact they could have on the organization. High-priority vulnerabilities are typically addressed first, followed by those with lower levels of risk.
Remediation Planning: Once vulnerabilities have been prioritized, a remediation plan is developed. This plan outlines the steps needed to address each vulnerability, including any software patches or updates that need to be applied, changes to system configurations or network settings, or other remediation activities.
Remediation Execution: With a remediation plan in place, the security team can begin implementing the necessary changes to address the identified vulnerabilities. This may involve applying software patches or updates, configuring security settings, or making other changes to the system or network.
Validation: After remediation activities have been completed, the system is retested to ensure that the vulnerabilities have been successfully addressed. This helps to confirm that the remediation efforts were effective and that the system is now more secure.
Ongoing Monitoring: Vulnerability remediation is an ongoing process that requires ongoing monitoring and testing to ensure that new vulnerabilities are identified and addressed in a timely manner. This may involve regular vulnerability scanning and risk assessments, as well as ongoing monitoring of system logs and other security data to identify potential threats.
Benefits of Vulnerability Remediation?
Implementing cybersecurity policies and practices to prevent attacks creates a secure digital environment for your system to operate in. In addition to that, there are particular advantages you can reap from carrying out vulnerability remediation.
You can also read: Broken Authentication Vulnerabilities: Explained
Save Costs From Attacks
As most things go, the cost of prevention is generally less than treating or managing the problem after the attacks. This holds with vulnerability remediation, which tries to find these threats before a cyber attack results in severe monetary damages.
For example, if your system is attacked by ransomware, then the cyber crooks may ask for big money in return for giving access back to your system. The cost of implementing the remediation to secure your system against vulnerabilities would definitely be much less than what the cybercriminal may demand.
Besides, paying the money to cyber crooks does not grant any guarantee of getting your system restored; hence, the impact would be much greater on economic grounds.
Gain Maximum Visibility
Vulnerability remediation is attained by conducting a deep scan of the existing and even future threats. You can identify and fix the threats on time through routine scans before they escalate, causing huge damage to your network.
Effective monitoring tools within an organization provide real-time information about threat vectors and their behavioral patterns. Reports from such tools are studied to make decisions in concrete terms and then take appropriate actions for shaping your security for the best.
Build a Standard Security Framework
The best security frameworks are standardized and repeatable, providing long-term benefits. Vulnerability remediation is a continuous, organized process. Once correctly set up, it can be automated to run continuously and save tremendous amounts of time and resources.
The remediation procedures are constant and reproducible across multiple systems to create the results as expected. In other words, through the same procedure, you can secure several digital assets, saving more of your time and resources.
Anticipate and Prevent Threats
In the world of cybersecurity, the party that makes the first move holds the advantage. Cybercriminals often succeed by catching their victims off guard. Even if you respond to attacks promptly, some damage may still occur.
You can also read: 5G Security Risks you should know
Vulnerability remediation is empowering through proactive security, giving you the upper hand. It allows you to know your enemy and eliminate potential threats before an intruder can take advantage of any vulnerability. Thus, you will be one step ahead of the cybercriminal and ultimately reinforce your general security posture.
Beat Cybercriminals With Vulnerability Remediation
Cybercriminals exploit poor links within systems in their favor to ensure entry. Vulnerability remediation puts you in the driving seat and lets you identify any weak spots within your network and patch them up before any intruder exploits them.
It is your choice to take advantage of vulnerability remediation or not. But sooner or later, the hacker would eventually find the weak points in your system. Wouldn’t you want to find these weaknesses and fix them before cybercriminals do?
Would you like to read more about vulnerability remediation-related articles? If so, we invite you to take a look at our other tech topics before you leave!