Numerous individuals attempt to pilfer corporate information. Instead of attacking fortified network security, these thieves concentrate on endpoint devices that can access enterprise networks.
Because endpoint devices are beyond the safeguard of a well-protected network, companies rely on their employees to use them securely. Therefore, it is imperative to implement endpoint security best practices to safeguard your network and corporate data.
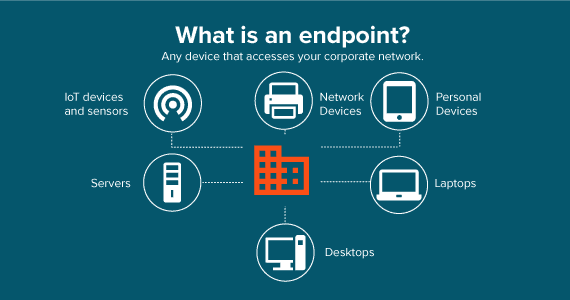
What is Endpoint Security?
Endpoint security refers to the protection of devices that are used to access an enterprise network, such as laptops, smartphones, tablets, and servers. These devices are referred to as “endpoints” because they are the points at which users interact with the network.
Endpoint security aims to prevent unauthorized access to the network through these devices, as well as to protect against threats such as malware, phishing attacks, and other cyber threats that can compromise the security of the network. Endpoint security solutions typically include antivirus and anti-malware software, firewalls, intrusion detection and prevention systems, and other security technologies that are specifically designed to protect endpoints.
Endpoint security is crucial in today’s digital age, where cyber threats are becoming increasingly sophisticated and pervasive. By implementing robust endpoint security measures, organizations can protect their networks and data from malicious attacks, minimize the risk of data breaches, and ensure the confidentiality, integrity, and availability of their critical business information.
Why Endpoint Security is Important
Your company’s security posture is weakened by unsecured endpoint devices that pose significant security risks.
Failure to adequately secure endpoints can leave them vulnerable to various security threats, such as malware attacks, social engineering attacks, drive-by downloads, data breaches, and device loss. According to a Ponemon Institute and Adaptiva report, on average, 48% of endpoint devices are at risk.
With an increasing number of employees working remotely, it is challenging to ensure that they adhere to cybersecurity best practices. For example, they may use public Wi-Fi networks in coffee shops without sufficient protection. To secure your IT infrastructure, implementing endpoint security best practices is essential.
Endpoint security is critical for several reasons:
- Protection from Cyber Attacks: Endpoint devices are often the first targets for cybercriminals attempting to infiltrate an organization’s network. By compromising a single endpoint device, an attacker can gain access to sensitive data and other network resources. Endpoint security solutions can help prevent these attacks by providing advanced threat detection and response capabilities, as well as real-time monitoring and reporting of potential security incidents.
- Prevention of Data Loss: Endpoint devices are frequently used to access and store sensitive data, including intellectual property, financial information, and customer data. Endpoint security measures can help prevent data loss by implementing access controls, data encryption, and other security measures that limit the risk of unauthorized access or data theft.
- Compliance with Regulations: Many organizations are subject to regulatory requirements that mandate specific data protection measures, such as HIPAA, GDPR, and PCI DSS. Endpoint security solutions can help organizations comply with these regulations by implementing the necessary security controls and ensuring that sensitive data is properly protected.
- Remote Workforce Management: With the rise of remote work, endpoint security has become even more critical. Employees working remotely may use their personal devices to access company data and resources, creating additional security risks. Endpoint security solutions can help manage and secure remote devices, ensuring that they meet the same security standards as on-premises devices.
In summary, endpoint security is critical for protecting an organization’s network, data, and reputation from cyber threats and ensuring compliance with regulations.
Endpoint Security Best Practices to Stay Safe
Here are the best practices for endpoint security to minimize security risks.
-
Install an Endpoint Security Solution
A reliable endpoint security solution safeguards endpoints against malware, viruses, malicious applications, and other harmful programs.
To ensure the protection of all endpoint devices, it is essential to install a dependable endpoint security solution like ESET Endpoint Security, Heimdal Threat Prevention Endpoint, or Bitdefender GravityZone.
-
Implement Encryption for Data Protection
To enhance endpoint protection, encrypt every hard drive connected to your network, as this adds an extra layer of security to your data and devices.
Encryption makes it difficult for cybercriminals to access sensitive data on an endpoint device if they obtain your company device.
Furthermore, if your employees use USB drives or other storage media for data transfers, it’s crucial to enable encryption on these devices as well.
-
Deploy Content Disarm and Reconstruction (CDR)
A content disarm and reconstruction (CDR) system is a useful tool that removes malicious content from files before sending them to recipients.
Threat actors often conceal malware, such as ransomware or remote access Trojans, in documents and send them to employees.
Installing a CDR on your endpoints guarantees that all known and unknown threats contained in documents are eliminated before they can harm an endpoint device.
-
Deploy a Clear BYOD Policy
The COVID-19 pandemic has led to a rise in remote working, resulting in increased usage of personal devices.
However, personal devices can pose a significant security threat as they may lack data encryption and other security capabilities. Additionally, personal devices are susceptible to being lost, which could lead to unauthorized users accessing sensitive data.
To secure business data, it’s crucial to establish a clear Bring Your Own Device (BYOD) policy, which encourages employees to use their personal devices safely.
-
Track All Devices Connected to Your Network
To safeguard your enterprise network from security threats, continuous monitoring of endpoint devices connected to it is crucial.
Take an inventory of all endpoints your company has, including company devices, employee-owned devices, IoT devices, and business phones. Utilize reliable endpoint management software to attain real-time visibility of devices on your network.
-
Regulate USB Port Access
USB ports can pose significant security threats if left unregulated. Threat actors can exploit these ports by executing various USB attacks, such as USB drop attacks, to compromise network security. Moreover, they can even cause irreparable damage to your endpoints by carrying out USB Killer attacks.
To mitigate the risks associated with USB drives, establish a strict policy against the use of unknown USB drives. If feasible, disable USB ports on endpoints within your company to safeguard against various USB threats.
-
Integrate Zero-Trust Network Access
By implementing Zero Trust Network Access (ZTNA), you can authenticate and authorize every endpoint device before granting access to your company’s resources.
ZTNA also limits access to specific services or applications within the network through an encrypted tunnel, effectively reducing the threat surface. As a result, in the event of an endpoint device being compromised, the threat actor will only have access to specific services or applications, not the entire network.
-
Update OS and All Software Regularly
Postponing operating system or software updates can significantly increase security risks. This is because hackers often exploit vulnerabilities in outdated operating systems and software to gain unauthorized access to end-user devices. Once they breach an endpoint, they try to infiltrate the entire enterprise network.
To mitigate these risks, implement a policy that requires all employees to update their PCs and software programs promptly as soon as updates become available. Failing to comply with this policy should result in some form of penalty.
Additionally, conduct random device audits to evaluate whether endpoint users are installing all the latest updates for their operating systems and software.
-
Implement Least Privilege
To enhance security and minimize the risk of data breaches, it is essential to implement the principle of least privilege. This approach entails giving users the minimum level of access necessary to perform their job functions.
By limiting user access to the network and IT resources, the damage a cyber attacker can cause in the event of a successful endpoint device compromise is significantly reduced. This approach can also help to improve operational efficiency, incident response, and minimize social engineering attacks.
-
Use Anti-Phishing Solutions
Phishing attacks are among the most prevalent cyberattacks, and they can be carried out with minimal resources. It’s crucial to implement a reliable anti-phishing solution to safeguard endpoints from such attacks. Additionally, conducting simulated phishing tests can help employees recognize and avoid actual phishing attacks.
-
Increase the Frequency of Employee Education Sessions
Most data theft and breaches occur due to human error. Implementing effective cybersecurity training programs is crucial in reducing endpoint security risks by educating employees about risky behavior. Therefore, develop a comprehensive cybersecurity training program for your employees.
To create a strong cybersecurity culture, avoid making training a once-a-year event. Instead, conduct multiple training sessions throughout the year. A cybersecurity training program should cover social engineering attacks, password hygiene, safe internet and email use, removable media, and different types of endpoint attacks. The topics you include may vary based on your organization’s threat landscape.
Endpoints is highly required to prevent Cyberattacks
To prevent endpoint attacks, it is crucial to take the necessary security measures due to the increase in ransomware attacks and data breaches. This is because threat actors persistently target endpoints to steal, encrypt, and exfiltrate sensitive data.
To achieve this, implement strong endpoint security solutions and ensure that endpoint security best practices are fully implemented. If your employees work remotely, it is also essential to understand the various security risks associated with remote work and how to mitigate them to protect your network.
Would you like to read more about EndPoint Security Best Practices to Stay Protected-related articles? If so, we invite you to take a look at our other tech topics before you leave!
![]()













